Mapping Security: A Complete Information to Security Maps and Their Functions
Associated Articles: Mapping Security: A Complete Information to Security Maps and Their Functions
Introduction
With enthusiasm, let’s navigate via the intriguing subject associated to Mapping Security: A Complete Information to Security Maps and Their Functions. Let’s weave fascinating data and supply recent views to the readers.
Desk of Content material
Mapping Security: A Complete Information to Security Maps and Their Functions

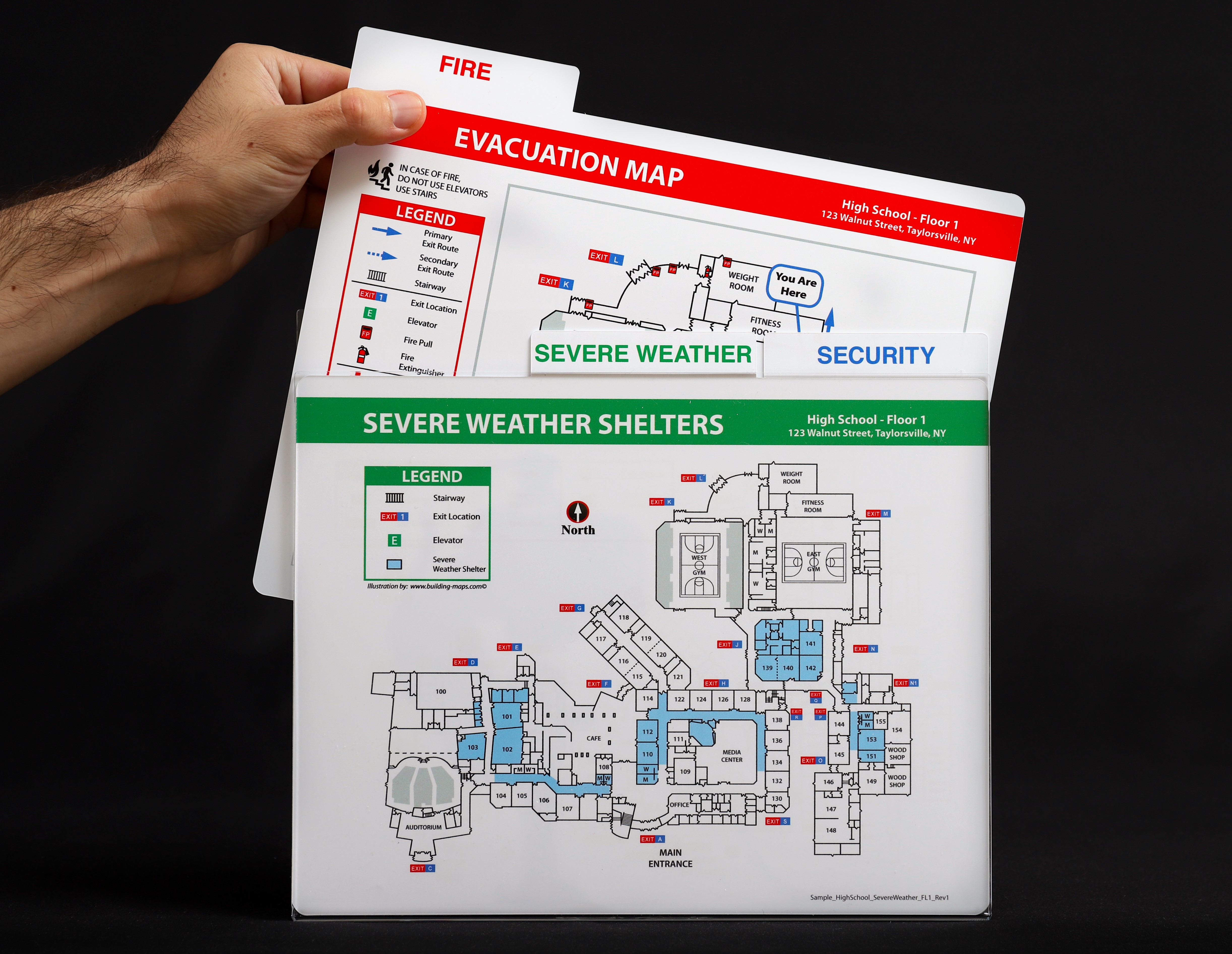
Security, in its broadest sense, encompasses the safety of people, property, and the surroundings from hurt. Successfully managing security requires proactive measures, and an important device on this endeavor is the protection map. Removed from a easy visible illustration of hazards, a security map is a dynamic, multifaceted useful resource that informs decision-making, improves response occasions, and finally contributes to a safer surroundings throughout various sectors. This text delves into the varied varieties of security maps, their creation, functions, and the advantages they provide.
Understanding the Scope of Security Maps:
A security map is a geographically referenced illustration of potential hazards, dangers, and security measures inside a particular space. This space can vary from a small office to a whole metropolis, a building website, a pure park, or perhaps a complicated industrial facility. The knowledge displayed on a security map varies relying on its function and the particular surroundings it depicts. Nonetheless, frequent parts embrace:
- Hazard identification: This includes pinpointing particular places of hazards, comparable to fireplace exits, electrical hazards, chemical spills, journey hazards, or areas vulnerable to flooding. The sort and severity of every hazard are essential elements of the mapping course of.
- Threat evaluation: Past easy hazard identification, security maps incorporate danger evaluation, contemplating the chance and potential penalties of every hazard. This enables for prioritization of mitigation efforts.
- Security measures: The map ought to clearly illustrate current security measures, comparable to fireplace extinguishers, emergency exits, first-aid stations, safety cameras, and designated evacuation routes.
- Emergency response data: This consists of contact data for emergency providers, designated meeting factors, and pre-planned evacuation routes.
- Accessibility data: For public areas, security maps can incorporate accessibility options like wheelchair ramps, accessible restrooms, and designated parking areas.
- Actual-time knowledge integration: Superior security maps can combine real-time knowledge feeds, comparable to site visitors data, climate updates, and sensor readings from varied gadgets, offering a dynamic view of the surroundings.
Forms of Security Maps:
Security maps usually are not one-size-fits-all. Their design and content material are tailor-made to the particular wants of the applying. Some frequent sorts embrace:
- Office Security Maps: These maps are essential for industrial settings, building websites, and workplaces. They element the situation of hazards, emergency tools, and evacuation routes particular to the office. They usually incorporate color-coding to focus on totally different hazard ranges.
- Group Security Maps: These maps deal with public security inside a group, exhibiting places of police stations, fireplace stations, hospitals, and crime hotspots. They’ll additionally spotlight areas vulnerable to pure disasters or different emergencies.
- Environmental Security Maps: These maps depict environmental hazards comparable to air pollution sources, areas prone to flooding or wildfires, and delicate ecosystems. They’re used for environmental danger administration and catastrophe preparedness.
- Transportation Security Maps: These maps deal with transportation infrastructure, highlighting areas with excessive accident charges, street hazards, and public transportation routes. They’re used for site visitors administration and bettering street security.
- Occasion Security Maps: For big-scale occasions like concert events or festivals, security maps are important for guiding attendees to emergency exits, first-aid stations, and designated gathering factors.
- Maritime Security Maps: These maps are utilized in marine environments, exhibiting navigational hazards, delivery lanes, and areas with potential environmental dangers.
Creating Efficient Security Maps:
The creation of a security map includes a number of key steps:
- Information Assortment: Thorough knowledge assortment is paramount. This includes conducting website surveys, reviewing current security documentation, and consulting with stakeholders.
- Hazard Identification and Threat Evaluation: This includes figuring out all potential hazards and assessing their chance and potential penalties. Varied danger evaluation methodologies may be employed.
- Map Design and Growth: Selecting the suitable mapping software program and choosing appropriate symbols and color-coding schemes is essential for creating a transparent and easy-to-understand map.
- Information Integration: Integrating related knowledge from varied sources, comparable to sensor networks, databases, and GIS techniques, enhances the map’s performance.
- Validation and Assessment: Earlier than deployment, the map must be totally reviewed and validated to make sure accuracy and completeness.
- Common Updates: Security maps usually are not static paperwork. Common updates are important to mirror modifications within the surroundings and to include new security measures.
Advantages of Utilizing Security Maps:
The implementation of security maps affords quite a few advantages:
- Improved Hazard Consciousness: Maps present a transparent and concise visible illustration of hazards, bettering consciousness amongst workers, residents, or occasion attendees.
- Enhanced Emergency Response: In case of an emergency, security maps facilitate fast and environment friendly response by guiding emergency personnel and directing people to security.
- Proactive Threat Administration: By figuring out and assessing dangers, security maps allow proactive danger administration methods, lowering the chance of accidents and incidents.
- Improved Communication: Security maps function a standard communication device, facilitating clear and constant communication about security procedures and hazards.
- Compliance with Rules: Many industries have security laws that require the usage of security maps.
- Price Financial savings: By stopping accidents and incidents, security maps contribute to important value financial savings in the long term.
- Information-Pushed Resolution Making: Security maps present priceless knowledge that informs decision-making concerning security enhancements and useful resource allocation.
Technological Developments in Security Mapping:
Technological developments have considerably enhanced the capabilities of security maps. The mixing of GIS (Geographic Info Techniques) know-how permits for the creation of subtle, interactive maps that incorporate real-time knowledge feeds. Cell functions and cloud-based platforms additional improve accessibility and value. Moreover, the usage of sensor networks, drones, and different applied sciences offers real-time knowledge on environmental circumstances and potential hazards, enhancing the accuracy and dynamism of security maps.
Conclusion:
Security maps are invaluable instruments for bettering security throughout various sectors. Their capacity to visually signify hazards, assess dangers, and information emergency response makes them an integral part of any complete security administration system. By leveraging technological developments and incorporating greatest practices, organizations can create efficient security maps that contribute to a safer and safer surroundings for everybody. The way forward for security mapping lies within the continued integration of superior applied sciences, fostering a extra dynamic, responsive, and data-driven strategy to security administration. As know-how continues to evolve, so too will the capabilities of security maps, additional enhancing their essential function in defending lives and property.







Closure
Thus, we hope this text has supplied priceless insights into Mapping Security: A Complete Information to Security Maps and Their Functions. We recognize your consideration to our article. See you in our subsequent article!